简单的英文,很容易懂,写得很清楚。
The only known IP address is the one from the gateway which is defined as “192.168.1.1” in this scenario. The gateway should act as a VPN server which only responses to connection requests. The gateway should be configured IP address independent to the client side. Therefore it is also impossible to pre-define security policies for any of the clients like it was done before.
First of all “racoon.conf” needs to be altered on the VPN gateway to accept requests from unknown or anonymous clients.
VPN gateway configuration: racoon.conf
There are some major points which have to be configured for a roadwarrior scenario:
· racoon should generate the security policy at runtime depending on the clients IP address which is connecting to the VPN gateway. This is done with the directive “generate_policy_on”. Therefore a setkey.conf is not necessary at all (except it is used to flush the databases)
· racoon should define proposals for anonymous clients which is done by the “remote anonymous” section.
· racoon should define security associations for anonymous clients. This is done by the “sainfo anonymous” section.
A basic racoon configuration may look like this. This example also shows some additional configurations compared to the previous examples. The explanation of the new commands is written within the configuration in italic style. These commands are not part of the configuration file itself.
path certificate "/etc/certs";
remote anonymous
No specific client is defined in the remote section. It has been anonymized to apply to all VPN-Clients.
{
exchange_mode aggressive,main;
The gateway accepts connections with phase 1 aggressive or main. certificate_type X.509 "HostA.public" "HostA.private"; my_identifier asn1dn; peers_identifier asn1dn; proposal_check claim; Compares lifetime and key length of initiator and responder and will choose the value from the initiator or responder which has a shorter lifetime or longer keylength. generate_policy on; This is very important for a roadwarrior configuration. racoon will generate Security Policies at runtime which will match to the connection requests of the roadwarrior clients. nat_traversal off; Defines whether NAT-Traversal is supported or not ike_frag on; If set to on, racoon will advertise itself as being capable of receiving packets split by IKE fragmentation [racoon_manual_06]. verify_cert off; passive on; Defines if a negotiation may be initiated or not. proposal { encryption_algorithm aes; hash_algorithm md5; authentication_method rsasig; dh_group 2; } } The proposal section remains unchanged. sainfo anonymous Like the remote section also the sainfo section must be altered to match security associations of anonymous clients. { pfs_group 2; lifetime time 1 hour; Defines how long a security association will be used. encryption_algorithm aes; authentication_algorithm hmac_md5; compression_algorithm deflate; } VPN gateway configuration: setkey.conf Like mentioned before, the VPN gateway should generate the SPD entries at runtime. Therefore setkey is obsolete. VPN client configuration: racoon.conf The client configuration only needs few modifications because in most cases the IP address of the VPN gateway is defined static and will not change. This does not apply to the “sainfo” section because usually it consists of the IP addresses of both peers. Because of the clients IP address being “unknown” the “sainfo” section must also be anonymized. The client configuration may look like this: path certificate "/etc/certs"; remote 192.168.1.1 { exchange_mode aggressive; In this scenario aggressive mode is initiated by the client for testing purposes. certificate_type X.509 "HostB.public" "HostB.private"; my_identifier asn1dn; peers_identifier asn1dn; proposal_check obey; The responder will obey the initiator anytime. nat_traversal off; ike_frag on; verify_cert off; proposal { encryption_algorithm aes; hash_algorithm md5; authentication_method rsasig; dh_group 2; } } sainfo anonymous { pfs_group 2; lifetime time 1 hour; encryption_algorithm aes; authentication_algorithm hmac_md5; compression_algorithm deflate; } VPN client configuration: setkey.conf In a roadwarrior scenario the client initiates the VPN connection. Therefore certain security policies must pre-exist which will cause the kernel to trigger racoon to establish a secure connection between client and VPN gateway. Like shown earlier this is done by entries in the SPD with the help of the “setkey” command. Usually source and destination IP addresses are written to the database but in this scenario the IP address of the client is unknown. Therefore it has to be set to its actual IP address dynamically or configured with a “blank” IP address to accept all possible IP addresses. A complete configuration of the Security Policy Database for transport mode may be configured with setkey like this: #!/usr/sbin/setkey -f # Flush SAD and SPD flush; spdflush; #SP for racoon spdadd 192.168.1.1 0.0.0.0 any -P in IPsec esp/transport//require; spdadd 0.0.0.0 192.168.1.1 any -P out IPsec esp/transport//require; Test of racoon roadwarrior connection. First of all the VPN gateway racoon daemon is started. As shown below no Security Policy Database entries exist on the VPN gateway.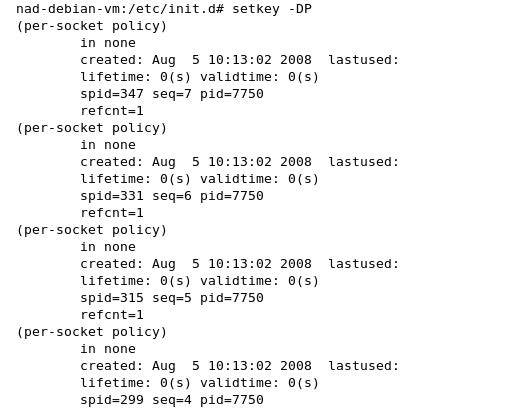 After this the client’s SPD is written and racoon is started. For testing purposes the clients IP address is changed[1] from 192.168.1.2 to 192.1.1.5 to prove that the server will establish a connection to an unknown IP address.
The first ICMP request ends up in an error displaying that the route to the destination Network (192.168.1.0) is unknown to the client because the client itself is configured being in the 192.1.1.0 network. Therefore a route must be set on the client’s side. This is done by the “route” command as follows:
# route add –net 192.168.1.0 netmask 255.255.255.0 eth1
In this rather basic scenario it is no problem to add this route permanently. In other scenarios, where a client needs different route because of different network communications the routes may be added dynamically at runtime. racoon itself has no option to add these routes automatically but has the capability to execute shell scripts at connection state “up” or “down”. This may also come in handy when SPD’s need to be generated or deleted at runtime.
After adding the route racoon established successfully the security associations between VPN gateway and client and encrypted the ICMP packets like shown as follows:
After this the client’s SPD is written and racoon is started. For testing purposes the clients IP address is changed[1] from 192.168.1.2 to 192.1.1.5 to prove that the server will establish a connection to an unknown IP address.
The first ICMP request ends up in an error displaying that the route to the destination Network (192.168.1.0) is unknown to the client because the client itself is configured being in the 192.1.1.0 network. Therefore a route must be set on the client’s side. This is done by the “route” command as follows:
# route add –net 192.168.1.0 netmask 255.255.255.0 eth1
In this rather basic scenario it is no problem to add this route permanently. In other scenarios, where a client needs different route because of different network communications the routes may be added dynamically at runtime. racoon itself has no option to add these routes automatically but has the capability to execute shell scripts at connection state “up” or “down”. This may also come in handy when SPD’s need to be generated or deleted at runtime.
After adding the route racoon established successfully the security associations between VPN gateway and client and encrypted the ICMP packets like shown as follows:
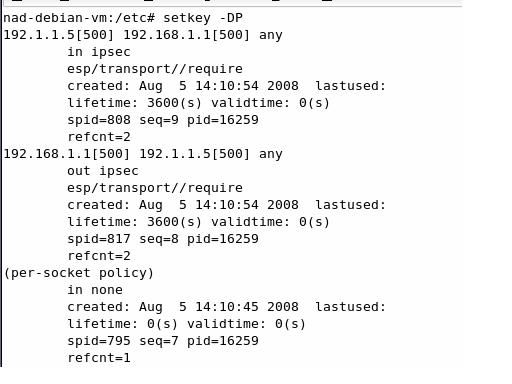
 On the gateway side racoon adds the Security Policy Database entries to the SPD:
On the gateway side racoon adds the Security Policy Database entries to the SPD:
 Changing an IP address is easily done by the “ifconfig” command which may be used as follows:
Changing an IP address is easily done by the “ifconfig” command which may be used as follows:
# ifconfig eth1 192.1.1.5 netmask 255.255.255.0 up
(eth1 is the active network adapter of the VM-Ware Client)
The gateway accepts connections with phase 1 aggressive or main. certificate_type X.509 "HostA.public" "HostA.private"; my_identifier asn1dn; peers_identifier asn1dn; proposal_check claim; Compares lifetime and key length of initiator and responder and will choose the value from the initiator or responder which has a shorter lifetime or longer keylength. generate_policy on; This is very important for a roadwarrior configuration. racoon will generate Security Policies at runtime which will match to the connection requests of the roadwarrior clients. nat_traversal off; Defines whether NAT-Traversal is supported or not ike_frag on; If set to on, racoon will advertise itself as being capable of receiving packets split by IKE fragmentation [racoon_manual_06]. verify_cert off; passive on; Defines if a negotiation may be initiated or not. proposal { encryption_algorithm aes; hash_algorithm md5; authentication_method rsasig; dh_group 2; } } The proposal section remains unchanged. sainfo anonymous Like the remote section also the sainfo section must be altered to match security associations of anonymous clients. { pfs_group 2; lifetime time 1 hour; Defines how long a security association will be used. encryption_algorithm aes; authentication_algorithm hmac_md5; compression_algorithm deflate; } VPN gateway configuration: setkey.conf Like mentioned before, the VPN gateway should generate the SPD entries at runtime. Therefore setkey is obsolete. VPN client configuration: racoon.conf The client configuration only needs few modifications because in most cases the IP address of the VPN gateway is defined static and will not change. This does not apply to the “sainfo” section because usually it consists of the IP addresses of both peers. Because of the clients IP address being “unknown” the “sainfo” section must also be anonymized. The client configuration may look like this: path certificate "/etc/certs"; remote 192.168.1.1 { exchange_mode aggressive; In this scenario aggressive mode is initiated by the client for testing purposes. certificate_type X.509 "HostB.public" "HostB.private"; my_identifier asn1dn; peers_identifier asn1dn; proposal_check obey; The responder will obey the initiator anytime. nat_traversal off; ike_frag on; verify_cert off; proposal { encryption_algorithm aes; hash_algorithm md5; authentication_method rsasig; dh_group 2; } } sainfo anonymous { pfs_group 2; lifetime time 1 hour; encryption_algorithm aes; authentication_algorithm hmac_md5; compression_algorithm deflate; } VPN client configuration: setkey.conf In a roadwarrior scenario the client initiates the VPN connection. Therefore certain security policies must pre-exist which will cause the kernel to trigger racoon to establish a secure connection between client and VPN gateway. Like shown earlier this is done by entries in the SPD with the help of the “setkey” command. Usually source and destination IP addresses are written to the database but in this scenario the IP address of the client is unknown. Therefore it has to be set to its actual IP address dynamically or configured with a “blank” IP address to accept all possible IP addresses. A complete configuration of the Security Policy Database for transport mode may be configured with setkey like this: #!/usr/sbin/setkey -f # Flush SAD and SPD flush; spdflush; #SP for racoon spdadd 192.168.1.1 0.0.0.0 any -P in IPsec esp/transport//require; spdadd 0.0.0.0 192.168.1.1 any -P out IPsec esp/transport//require; Test of racoon roadwarrior connection. First of all the VPN gateway racoon daemon is started. As shown below no Security Policy Database entries exist on the VPN gateway.
 After this the client’s SPD is written and racoon is started. For testing purposes the clients IP address is changed[1] from 192.168.1.2 to 192.1.1.5 to prove that the server will establish a connection to an unknown IP address.
The first ICMP request ends up in an error displaying that the route to the destination Network (192.168.1.0) is unknown to the client because the client itself is configured being in the 192.1.1.0 network. Therefore a route must be set on the client’s side. This is done by the “route” command as follows:
# route add –net 192.168.1.0 netmask 255.255.255.0 eth1
In this rather basic scenario it is no problem to add this route permanently. In other scenarios, where a client needs different route because of different network communications the routes may be added dynamically at runtime. racoon itself has no option to add these routes automatically but has the capability to execute shell scripts at connection state “up” or “down”. This may also come in handy when SPD’s need to be generated or deleted at runtime.
After adding the route racoon established successfully the security associations between VPN gateway and client and encrypted the ICMP packets like shown as follows:
After this the client’s SPD is written and racoon is started. For testing purposes the clients IP address is changed[1] from 192.168.1.2 to 192.1.1.5 to prove that the server will establish a connection to an unknown IP address.
The first ICMP request ends up in an error displaying that the route to the destination Network (192.168.1.0) is unknown to the client because the client itself is configured being in the 192.1.1.0 network. Therefore a route must be set on the client’s side. This is done by the “route” command as follows:
# route add –net 192.168.1.0 netmask 255.255.255.0 eth1
In this rather basic scenario it is no problem to add this route permanently. In other scenarios, where a client needs different route because of different network communications the routes may be added dynamically at runtime. racoon itself has no option to add these routes automatically but has the capability to execute shell scripts at connection state “up” or “down”. This may also come in handy when SPD’s need to be generated or deleted at runtime.
After adding the route racoon established successfully the security associations between VPN gateway and client and encrypted the ICMP packets like shown as follows:
 On the gateway side racoon adds the Security Policy Database entries to the SPD:
On the gateway side racoon adds the Security Policy Database entries to the SPD:
 Changing an IP address is easily done by the “ifconfig” command which may be used as follows:
Changing an IP address is easily done by the “ifconfig” command which may be used as follows: # ifconfig eth1 192.1.1.5 netmask 255.255.255.0 up
(eth1 is the active network adapter of the VM-Ware Client)